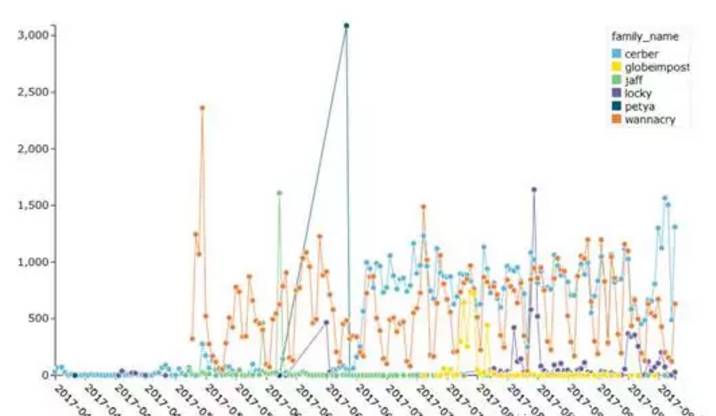
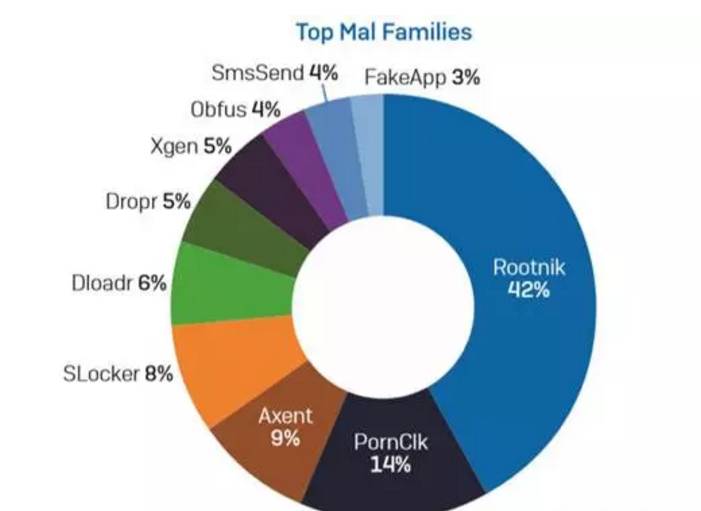
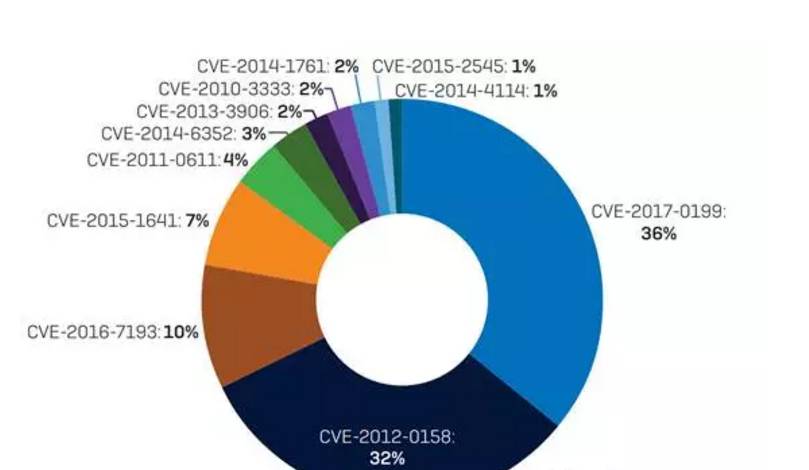
Recently, Sophos announced the 2018 malicious code epidemic analysis report to predict possible malicious code threats in 2018 by analyzing security threat events since 2017. They believe that the four major trends presented by malicious code in 2017 may become the main behavior in 2018. 1 WannaCry pioneered RaaS's ransomware service model Prior to WannaCry, ransomware Cerber has been at the forefront of ransomware-like malicious code. Since WannaCry used the "Eternal Blue" vulnerability to impact the entire Earth Internet, WannaCry has accounted for half of all ransomware. Although Cerber fell to second place, the power behind it was neglected, and Cerber's makers constantly updated and nurtured new variants to adapt to the changing network environment, such as sandbox detection and evasion in Cerber. The following picture shows the outbreak trend of the 2017 ransomware. It can be seen that there is a clear peak around June. This period is the outbreak of WannaCry and NotPetya. In the middle and late period, it is mainly the rise of Locky, but you can find Cerber in the whole extortion. The software has always existed steadily, which also illustrates the attack capability of Cerber from another aspect. Ransomware is currently the largest trading project on the dark network. In 2017, a customized service model appeared. Even some ransomware software has a marketing model similar to MLM. After a person is blackmailed, as long as the ransomware is forwarded to 10 The above WeChat group or community group can decrypt their own systems. This trend will become more apparent in 2018. Health care, government and key infrastructure, education industry may still be the hardest hit by extortion. 2 Android malicious code Android malicious code in 2017 increased by 17.6% compared to 2016. Among them, Rootnik is the most popular malware family, POrnclk takes the second place, and the rest are Axent, Slocker and Dloader. Interestingly, many apps on GooglePlay are linked to the Battlenik Rootnik, which was also discovered in late September to exploit the DirtyCowLinux vulnerability. The number of threats found on Googleplay has doubled since the same period in 2016: more than 800 Android apps are infected with Xavir malware, and WireX has more than 100 infected countries and more than 140,000 devices. Wirex gets its DDoS attack target from u.axclick.store. Then create a Webview and get the target hostname and port. Then start 50 threads to launch the attack. Each thread sends 10,000,000 512 bytes of data. 3 MAC malicious code Most people have always believed that Mac systems are more secure than Windows. From the situation found in 2017, there are so many malicious code for Mac system, but the actual number of attacks is not high, but a trending zombie of 2018 will be huge for Mac's junk or advertising-like malicious code. 4 Threat from windows office The following picture shows the distribution of office vulnerabilities that have been exploited since 2017. Interestingly, CVE-2012-0158 is not the most commonly used Offce vulnerability, but it is called "undead vulnerabilities" by some people, from 2012. Disclosure has been used to a large extent. Since 2017, CVE-2017-0199 has become the most vulnerable vulnerability for attackers. CVE-2017-0199 security vulnerabilities are available in multiple versions of Microsoft Offce. However, some people predict that the next one should be CVE-2017-11826. Finally, Xiao Bian believes that Sophos also missed an important prediction point, that is, the malicious code threat of the Internet and the industrial control system in the post-Mirai era! From the analysis of the Internet of Things malicious code analyzed and reported by Malware Benchmark in 2017, the malicious code such as IOTroop, Satori and Rowdy is based on the source code of mirai. After continuous variation and improvement, it has evolved from the traditional Linux platform to the Windows platform. Ports are also changing, from traditional weak password attacks to integrated attacks with weak passwords and exploits. The rapid and rich evolution of such an attack method is doomed to be calm in the industrial control Internet of Things in 2018! Crystal head is an important interface equipment in network connection. It is a kind of plastic joint which can be inserted along the fixed direction and can automatically prevent falling off. It is used for network communication. It is named "crystal head" because of its crystal like appearance. It is mainly used to connect network card port, hub, switch, telephone, etc. The two ends of each twisted pair are connected with network card and hub (or switch) by installing crystal head. Modular Plug ShenZhen Antenk Electronics Co,Ltd , https://www.antenksocket.com