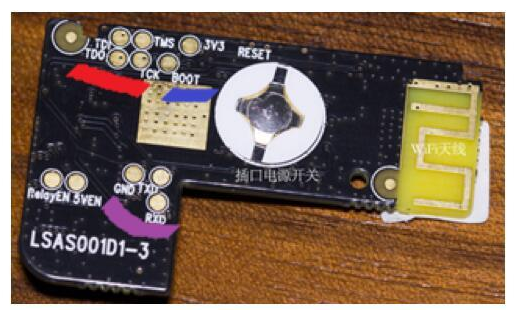
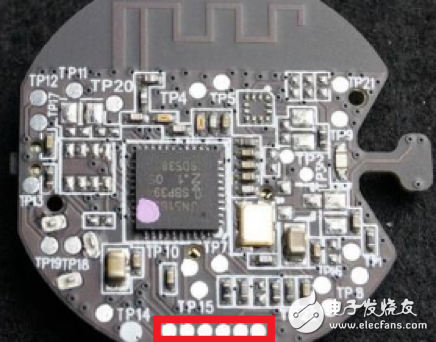
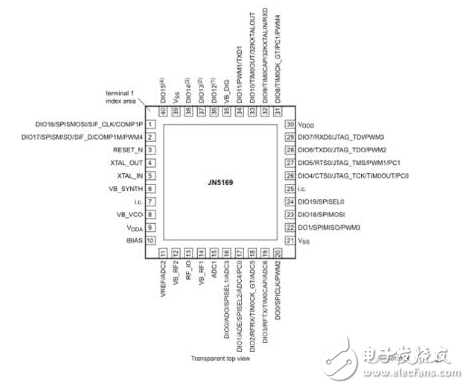
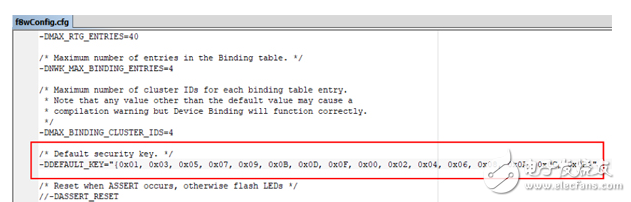
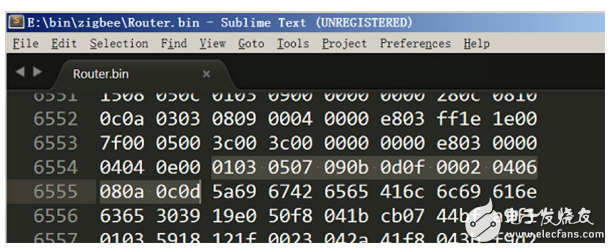
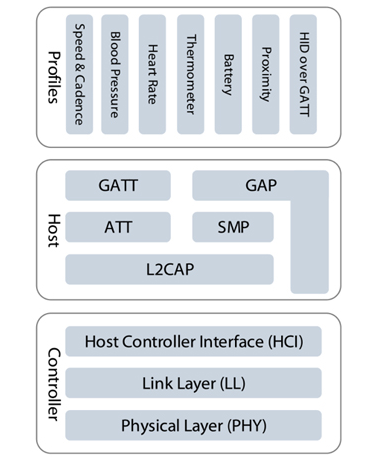
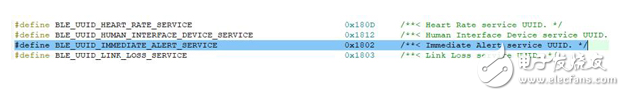
IoT devices have security risks because they expose enough sensitive information to be exploited by attackers to create attacks. These sensitive information can be divided into two categories according to the location of exposure: one is the firmware stored in the device and the information printed inside the product (such as PCB silk screen, chip model); the other is transmission in the network. (not just Ethernet, Wi-Fi, Bluetooth, etc.) information. This paper introduces the security risks of weak devices in the Internet of Things from the perspectives of local information and network information, and then proposes a method for equipment reinforcement. In recent years, with the rapid development of Internet of Things technology, the number of Internet of Things products is also exploding. Gartner predicts that after two years, the installed capacity of IoT devices will exceed 20 billion [1], and the amount of information brought by these IoT devices will be very large. At the same time, information security risks caused by IoT devices are also increasing year by year, and even some hidden dangers have caused irreparable damage, such as the Mirai event at the end of 2016 [2], because of the large number of Internet of Things exposed on the Internet. The device has weak passwords and unrepaired vulnerabilities. On March 27, 2018, the NSFOCUS 2017 Internet of Things Security Annual Report [3] was released, which analyzed the exposure of IoT assets, the vulnerability of IoT devices, and the threat risks of IoT devices. The Internet of Things security protection system is given. IoT devices have security risks because they expose enough sensitive information to be exploited by attackers to create attacks. These sensitive information can be divided into two categories according to the location of exposure: one is the firmware stored in the device and the information printed inside the product (such as PCB silk screen, chip model), etc. Local information; the other is information that is transmitted over the network (not just Ethernet, Wi-Fi, Bluetooth, etc.). At present, it seems that whether it is a manufacturer or a user, the concern about the security of weak devices is not very sufficient. For example, in the XPwn2017 Future Security Exploration Event [4] in September 2017, a hacker reversed a single-chip program that shared a bicycle, thus exploiting a loophole. In October 2017, IoT security researchers infiltrated the Zigbee network of LIFX smart light bulbs [5] and reversed the firmware of the device to obtain their Wi-Fi network password. It can be seen that there are many security risks in IoT devices, and we are faced with a challenge: how to eliminate these security risks. This article takes weak devices as an example to illustrate how to harden weak devices and solve the security risks that have already occurred. In the following sections, the author will first introduce the security risks of weak devices in the Internet of Things, and then introduce the methods and recommendations for the reinforcement of IoT devices, and finally summarize them briefly. Typically, an attacker gathers enough information to exploit an existing vulnerability or exploit a new vulnerability to launch an attack on the device. If the attacker does not get the information that can be used, the security risks of the device will not exist. What information is generally exposed by IoT devices? From the unknown of information, it can be divided into two types: local information and information in the network. Next, the security risks of the weak devices of the Internet of Things will be introduced from these two aspects. Local information Local information, defined here, is information that can be obtained directly from product contact operations by purchasing equipment, observing, or using tools. Generally include PCB silk screen, hardware interface, firmware information, etc. (1) PCB silk screen The Chinese name of the PCB is printed circuit board. In the process of designing and manufacturing PCB, silk screen printing brings great convenience to engineers' welding and debugging work. However, after the product is shipped, the PCB silkscreen information on it does not help the user, but provides information for the attacker's successful cracking. Taking the Wi-Fi smart socket [6] shown in Figure 1 as an example, on the PCB, the socket exposes three types of sensitive information: JTAG debug interface (red marked position), UART interface position (purple marked position), and settings. The BOOT of the program start position (the position of the blue mark). JTAG and UART are two types of interfaces that chip vendors provide to engineers to read and download programs. Attackers can also use these two types of interfaces to try to read the firmware. For its specific reading and downloading methods, refer to "Key Technology for Penetrating Low-Performance Intelligent Devices - Firmware Extraction" [7]. Figure 1 - Silkscreen information on a smart socket PCB (2) Hardware interface and chip information The JTAG and UART interface information has been mentioned in the previous section. In fact, these two types of interfaces are most helpful to the attacker, because only a few tools are needed to read the firmware information in the device and analyze more information. Figure 2 - A smart device PCB Taking the PCB shown in Figure 2 as an example, it is easy to find the six pads (red box marks) that are regularly arranged. Combined with the model information on the chip (JN516x), it is easy to find it in the chip manual [8]. The pin diagram of the chip and the firmware download mode of the chip are shown in Figure 3. Figure 3 - Chip Pin Diagram for JN5169 According to Figure 3, combined with the multimeter, it can be tested whether the pins of the six pads and the chip are directly connected (short-circuit test). If it is directly connected, it can be determined that the interface is used to download the program. In fact, the interface used by the chip JN5169 downloader requires a total of six. The attacker locates the information required by the program download interface, but simply disassembles the article by searching for the device, or buys the device and disassembles it to obtain it. The purpose of the attacker to obtain this information is very clear: get the firmware to analyze more information or exploit the network communication related vulnerabilities. (3) Firmware information The firmware contains almost all the information except the network information, including the program execution flow, initialization parameters, and so on. If the content of the two parties' communication is encrypted at the beginning, information such as initial or default encryption parameters (such as key, initial vector) will be encoded into the firmware. For example, in the Z-Stack protocol stack, the default key for Zigbee communication is hard coded, as shown in Figure 4 and Figure 5. If you go deeper, generate multiple firmware in the IAR compiler environment, analyze the location of the key, you will find that the location of the key is more regular. Figure 4 - Default Key Information in Z-Stack Figure 5 - Default key used by Zigbee communication in firmware compiled from Z-Stack 2. Network information There are two types of information in the network, one is information for control, and the other is information for sharing and storage. Generally, if there is a hidden danger in the network information, it indicates that the former may have hidden dangers of device out of control, or the latter may have hidden dangers of privacy leakage. Generally, there are several types of attacks in the network: Replay: Bluetooth, Wi-Fi and other protocols, application layer control messages for cloud management. Plain text: The application of insecure protocols such as the HTTP protocol leads to the disclosure of sensitive information and the control of devices. Dos: A denial of service attack that prevents the device from providing network services. Next, the author takes the low-power Bluetooth protocol stack as an example to briefly introduce the hidden dangers of control information and storage/shared information in the network transmission process. The low-power Bluetooth protocol stack, like other protocol stacks, can also be understood using a layered model. In general, manufacturers of low-power Bluetooth chips will introduce the protocol stack in the chip manual and summarize a similar layered model. The model summarized by Nordic [9] is shown here. As shown in Figure 6, it can be divided into three layers. The bottom layer is Controller, the middle layer is Host, and the top layer is Profiles. Figure 6 – Low-Power Bluetooth Protocol Stack Layered Model There is no in-depth analysis of the protocol stack here, but the GATT part needs to be noted. When the Bluetooth device communicates at the GATT layer, the two parties can understand the client and the server. When the two establish a connection, they can read and write to each other's services (identified by the UUID). E.g: Figure 7 - Predefined UUIDs in the Stack Two examples are introduced, which represent that the control information is utilized, and the information used for sharing and storage is illegally acquired. In general, if a value is written to a service with a UUID of 0x1802, it will cause a device alarm. If the low-power Bluetooth device (A, the product actually used by the user) does not authenticate the Bluetooth device (B, computer, mobile phone and other dual-mode Bluetooth devices) used by the attacker, the attacker is very easy to use B to attack A. A successful write will cause a device abnormal alarm. Similarly, the data in the service with the UUID of 0x180D in the A device can also be read to obtain the heart rate of the user (provided that the information is not encrypted). In fact, the communication process of some manufacturers' wristband products is not encrypted, resulting in device control or privacy information leakage. In general, the vulnerability mining process involves code auditing, black box testing, document research, and so on. The weak device hardening method in this section will ensure that the attacker cannot perform code auditing on the weak device to ensure that there is no valuable information in the black box test result. Therefore, the author proposes that the purpose of the protection method is clear: to prevent the attacker from obtaining information such as source code, firmware, and port. The method of disabling this information disclosure is straightforward and can be divided into two steps: information read protection settings and information encryption settings. This ensures that the information is unreadable (invisible) and that it is extremely difficult to decrypt even if read. 1. Information unreadable method (1) For PCB: Generally, there are silk screen, interface, chip model and other information on the PCB, which provides convenience for the attacker to find the firmware extraction interface. As shown in Figure 1, the exposed JTAG, UART, and BOOT mode selection interfaces enable the attacker to target the firmware. Therefore, it is recommended that the development engineer remove the PCB silk screen, chip model and other information, and remove the interface to download the firmware. However, this does not solve the problem fundamentally. If the attacker is familiar with the package of the master chip, the test can always be matched. (2) For firmware-MCU internal: The weak device consists of a control chip and peripheral modules (such as sensors, networking modules, etc.), and the code is in the control chip or on the networked control chip or in the networking module. The firmware can be made unreadable. The storage device has read protection capabilities. You can make the contents of the memory unreadable by setting some read protection options. Take the common STM32f1 series of microcontrollers as an example. The internal flash read protection option of the microcontroller can be changed by setting the value of the RDP (Global Read-out ProtecTIon) register. When the read protection option is enabled, the firmware of the microcontroller cannot be read out via the JTAG and UART interfaces. That is to say, the chip structure must be destroyed, and it is possible to read out the program inside the chip. Figure 8 – RDP function of the STM32f1 series of microcontrollers Similar functions are not only found in ST's chips, but also NXP's CRP (Code Read ProtecTIon), TI's FMPRE register. To achieve this security capability, the product development team needs to invest enough energy in the MCU's read protection strategy to ensure code security. (3) For firmware-MCU outside: For weak devices, the firmware outside the MCU is currently stored in a dedicated ROM chip, such as the W25Q128 series in the SOP8 package that communicates on the SPI bus, as shown in Figure 9. Figure 9 – Flash Chip in SOP8 Package Generally, the reason why the Flash chip is selected as the memory for storing the firmware is because the Flash capacity integrated in only one MCU is insufficient to ensure the complete transplantation of the protocol stack. Therefore, it is recommended that the code of the protocol stack be separated from the code related to the product business, run the business-related code in the MCU, and use the read protection function to enable the business code to be unreadable. If necessary, you can partially encrypt and confuse the code of the protocol stack to prevent attackers from performing reverse analysis or vulnerability mining. 2. Information encryption The more secure encryption algorithm is RSA, and according to the current development of MCU, it is not difficult to implement RSA encryption system in MCU. For example, the IEEE 802.15.4 wireless chip cc2538 integrates the ECC RSA-2048 accelerator, which can improve the working efficiency of the MCU under the RSA cryptosystem; ST provides the Cryptographic Library. From the performance of the current chip, RSA encryption on weak devices is not a problem. (1) Protocol stack Taking the lwip protocol stack as an example, in the official document of the protocol stack, the content about the encrypted transmission cannot be found. Therefore, it is necessary to integrate the secondary encryption function of the protocol, as shown in FIG. Ideally, RSA and AES hybrid encryption methods are used: RSA is used to encrypt and transmit AES keys, and then AES encryption is used for data transmission. Because the public key stored on the device side has no decryption capability, it is very difficult to decrypt the AES key based on the ciphertext and the public key. The attacker cannot obtain the decryption key, and there is no way to decrypt the information, thereby ensuring the information. The security of the transmission. Figure 10 - Features of the lwip Stack (2) Application layer communication There are three methods for application layer hardening: encrypting data transmitted by the application layer, turning off unnecessary port opening, and black and white list policy. Encrypting the data transmitted by the application layer can solve a series of problems caused by the decryption of the Bluetooth packet mentioned in Section 2.2. The Android phone can capture and save the Bluetooth communication process in the form of a log. After saving, the log file can be opened for analysis by using tools such as wireshark, and the data packet is decrypted by the Bluetooth protocol stack. If the content of the message transmission is clear in the product development process, it will lead to the disclosure of information (gatt description information and values, etc.). At this point, encryption (still using RSA and AES encryption) is a good way to prevent hackers from performing encrypted replays. As a weak device, it is necessary to close unnecessary ports as much as possible. I recommend not opening the port. The weak device and the cloud exist as a client role in the interaction process. A good black and white list mechanism can ensure that the communication object of the device is legal. These two methods are not covered in depth here. This paper introduces the security risks of weak devices in the Internet of Things from the perspectives of local information and network information, and then proposes a method for equipment reinforcement. In general, the idea of ​​weak device protection is relatively simple, that is, to eliminate redundant information. As long as the manufacturer's product design and development process are relatively standardized, there are few or no safety hazards in the product. Organic Light Emitting Diode,Pm Oled,Oled For Medical Products,Stepper Motor Oled ESEN Optoelectronics Technology Co., Ltd, , https://www.newvisionlcd.com